To support Inde customers throughout 2023's Cyber Smart Week we will be publishing a blog post each day that details a category of mitigation that you can implement to harden yourself against popular adversary techniques. These blogs are to help technical managers and practitioners get a better grasp on how to manage security risks within their business. Our selection is based upon our practical experience in responding to incidents, researching threat actors and adversary simulation engagements.
Today we'll discuss Tiered Admin Access.
Lateral Movement
To achieve their objective, intrusions depend upon viable paths existing between hosts. If threat actors are unable to extend their compromise within a network, they are unlikely positioned to achieve their intended objective. When system administrators approach this dilemma, network segmentation is frequently the solution seen fit to address it. However, there are limitations to this:
- Business operations will still require some level of access between segments, and this may involve protocols and services such as HTTP/S, RDP, SMB and WinRM - all of which have the potential to be used for remote code execution (and thus movement between hosts). For example, to authenticate against the domain, all hosts must connect to domain controllers on a variety of ports.
- It's still rare to see isolation within subnets, meaning hosts within them can connect to one another on any port permitted by the host firewall - which is typically everything.
Unless privilege management has also been considered - and even if it has - then you'll often see the use of elevated domain privileges outside of domain controllers. Combined with viable paths in the network, there is still the risk of potentially trivial opportunities to elevate domain privileges. It is these pathways which we seek to identify and exploit in our adversary simulation engagements, and the same that threat actors use to extend compromise across an estate.
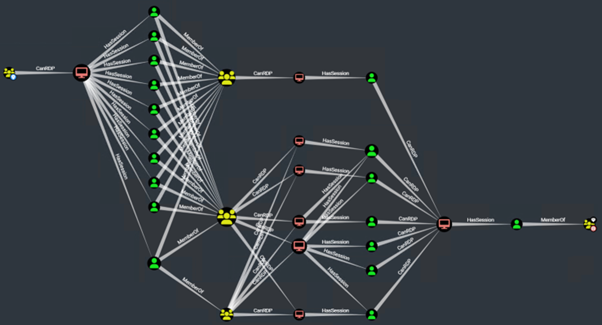
BloodHound graph showing elevation paths
Domain Tiers
When considering privilege management within a Windows domain, three tiers exist with distinct functions:
- Tier 0: Identity management plane. This includes domain controllers, Okta/Entra sync servers and a small number of systems that have effective control of identity.
- Tier 1: Enterprise servers, services, and applications.
- Tier 2: Desktops, laptops, printers, and other user devices.
Users may act in the higher-privileged tier if authorised to do so, however privileged accounts may not act in lower-privileged tiers.
Visually, this would look like:
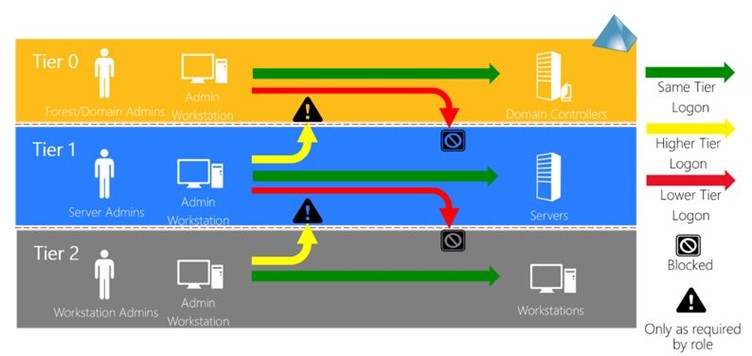
Source: Microsoft
In Practice
The primary goal of the tiered administrative model is to segregate high-privilege activities from high-risk zones, effectively eliminating paths of privilege escalation or making them significantly more difficult to identify and follow. When our actions impose cost upon threat actors and force them to take greater risks to achieve their objectives, we are afforded more detection opportunities. When properly implemented, compromise of a tier is confined to it as higher-privilege credentials are not exposed to it. For domain administrators this is achieved by:
- Confining the use of domain admin accounts to domain controllers.
- Using user rights assignment to deny domain admin accounts the ability to interactively log on to member servers and workstations.
- Issuing domain admin privileges to only those who are required to administer the domain.
- Servers and workstations may be administered:
- Using dedicated server and workstation admin accounts.
- Or using LAPS to manage local admin accounts and granting LAPS read access to those who require it.
- Using user rights assignment to deny server admin accounts the ability to interactively log on to workstations.
Optionally, access to higher-privileged tiers (e.g. tier 1 to tier 0) may also be forced through dedicated, hardened jumphost.
And as matters of general hygiene:
- Grant group membership to only those who require it – particularly groups which grant elevated rights.
- Do not leave RDP sessions disconnected. Always sign them off. Group policy is available to address this.
- Harden devices against credential access methods.
- Leverage tools such as CrowdStrike Identity Threat Detection or PingCastle to identify AD misconfigurations.
Privileged Identity Management (PIM), and Privileged Access Management (PAM) tooling such as CyberArk, can also be used to request rights as required. These allows for more granular control over elevated privilege requests, such as automatically revoking after a given time, or requiring approval to activate.
Further Reading
SpecterOps: Establish security boundaries in your on-prem AD and Azure environment

COMMENTS